Today, where technology drives most healthcare operations, secure patient data management is more critical than ever. Patient records often contain highly sensitive information, including medical histories, personal details, and insurance data, which makes them a prime target for cybercriminals. Therefore, a single data breach can have devastating consequences—not just for the patients, whose privacy and safety may be compromised, but also for healthcare providers, who may face legal repercussions, financial losses, and irreparable damage to their reputations.
Therefore, regulatory frameworks like the Health Insurance Portability and Accountability Act (HIPAA) in the United States and the General Data Protection Regulation (GDPR) in Europe have been established to mitigate these risks. These laws set stringent guidelines for handling, storing, and sharing patient information. This blog discusses the importance of secure patient data management and how healthcare providers can adopt PULSE to mitigate risks and maintain compliance with these critical regulations.
Table of Contents
The Importance of Regulatory Compliance in Patient Data Management
In this digital world, healthcare providers handle unprecedented patient data. From electronic health records to wearable devices that track vital signs, the data ecosystem is vast, complex, and sensitive. Therefore, with this increased accessibility comes a critical responsibility: protecting patient information while adhering to regulatory frameworks designed to safeguard privacy.
However, compliance is more than a legal obligation; it demonstrates a commitment to patient welfare. When patients feel confident that their information is treated with care and respect, they are more likely to engage openly with their providers. This transparency facilitates better communication, more accurate diagnoses, and improved health outcomes. Therefore, regulatory compliance is more than just following the rules—it is a strategic investment in building enduring relationships with patients.
How to Build a Robust and Secure Infrastructure
A strong foundation for physical and digital security can safeguard sensitive data and protect critical systems from potential breaches. On the physical side, this means creating secure server rooms with restricted access, where only authorized personnel can enter.
On the digital front, a multi-layered approach to security is critical. This includes firewalls, which act as the first line of defence and block unauthorized access. Intrusion detection systems also add another layer of vigilance by constantly monitoring networks for unusual activity.
In addition, encrypting data in transit and at rest protects it from unauthorized access, as it remains unintelligible even if intercepted. This commitment to robust Encryption protects information shared across networks and stored in databases.
Therefore, by precisely addressing both physical and digital security needs, organizations can create an infrastructure that minimizes vulnerabilities and safeguards critical information.
Role-Based Access Control (RBAC)
At its core, RBAC organizes users into roles based on their responsibilities. Each role is assigned predefined permissions that dictate what information and resources they can interact with. For example, a radiologist requires access to diagnostic imaging records but doesn’t need to view billing information. Similarly, a billing officer may handle financial data but has no reason to see sensitive medical histories.
This precise delineation supports data security and streamlines workflows. When each role has access only to the data they need, it reduces clutter and confusion.
Principles of Least Privilege
This concept dictates that users have the minimum access necessary to perform their duties. For example, a medical intern may need to review patient charts for educational purposes but is unable to modify treatment plans. By restricting privileges in this way, healthcare systems can protect sensitive data from accidental or intentional misuse.
This principle is particularly valuable in large hospital networks, where employees often shift between departments. Transitions are seamless when roles and access are clearly defined and potential data vulnerabilities are minimized.
The Power of Encryption in Healthcare
Encryption converts sensitive information into unreadable formats that can only be deciphered with the correct encryption key. Advanced Encryption Standard (AES), a globally recognized encryption protocol, is often the backbone of healthcare data security. Transport Layer Security (TLS) also adds another layer of protection by encrypting data exchanged over networks. This is particularly vital in telehealth consultations, where sensitive patient conversations and records are exchanged.
Besides, secure messaging platforms like PULSE, designed for healthcare, facilitate real-time communication while maintaining privacy standards.
What is PULSE and How it Facilitates Secure Patient Data Management
PULSE is a patient-provider unified ledger built on blockchain or distributed ledger technology (DLT) to create a unified record of patient-provider interactions. This ledger upholds data integrity, enhances interoperability, and enables seamless collaboration among patients, providers, and other stakeholders, all while prioritizing privacy and security.
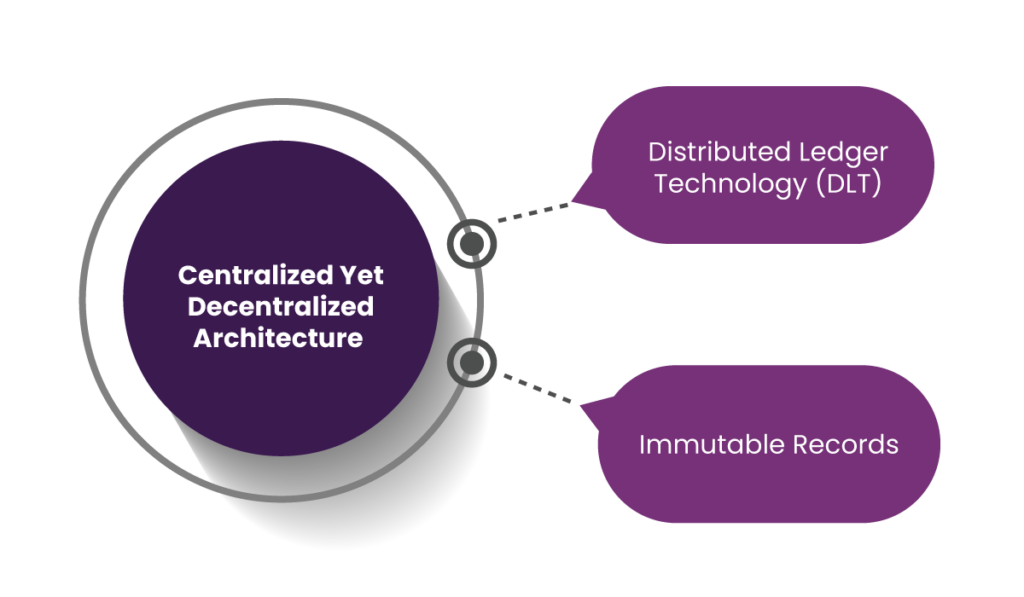
1. Centralized Yet Decentralized Architecture
PULSE leverages Distributed Ledger Technology (DLT) to balance decentralization with a unified data framework. This innovative approach improves patient data management by boosting transparency, trust, and accessibility. Let’s break down the core features and their impact on patient-provider relationships.
a. Distributed Ledger Technology (DLT)
The decentralized nature of DLT eliminates the monopolistic control of a single entity over patient data. While no one party has exclusive ownership, the system maintains a unified, comprehensive view of all patient records.
b. Immutable Records
Every interaction between patients and providers is permanently recorded in the ledger. This tamper-proof history serves as an unalterable record of medical events and decisions. As a result, patients can easily track their care history, diagnoses, and treatments. Thus, reliable records diminish patient and provider misunderstandings and disagreements and create a smoother care experience.
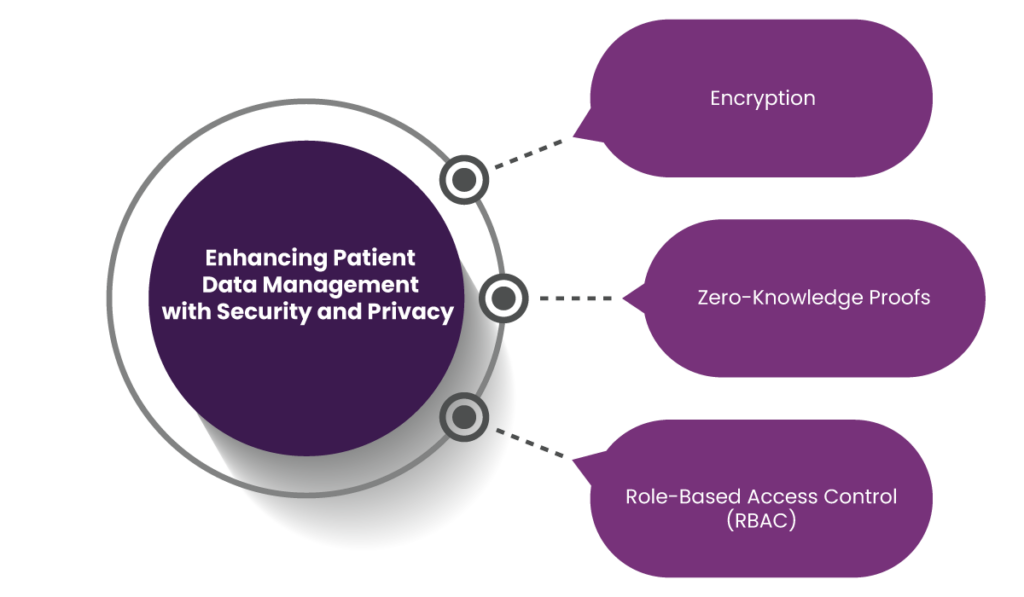
2. Enhancing Patient Data Management with Security and Privacy
Here’s a detailed breakdown of how PULSE keeps patient data safe:
a. Encryption
PULSE uses advanced cryptographic protection methods to prevent unauthorized access to personal data during transmission or storage. Therefore, patients are more likely to engage actively with digital healthcare platforms when they feel their information is protected from cyber threats.
b. Zero-Knowledge Proofs
Zero-knowledge proofs (ZKP) allow systems to verify data without exposing other sensitive details. This approach facilitates transparency and data verification without risking overexposure.
c. Role-Based Access Control (RBAC)
As mentioned earlier, RBAC organizes access to patient data based on specific roles. For patients, this offers peace of mind that their data is not freely accessible to everyone within the system.
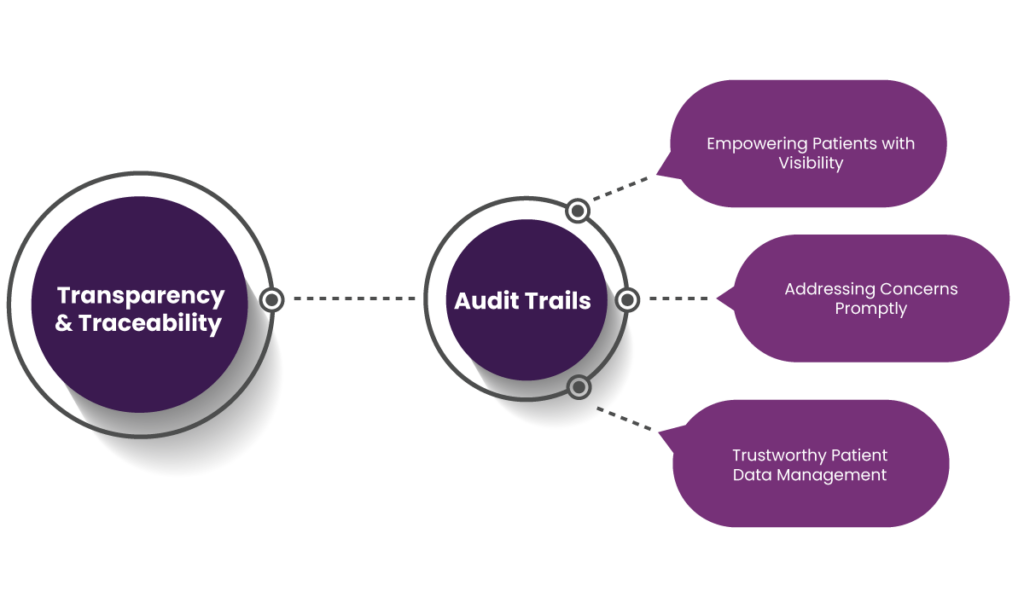
3. Transparency and Traceability
a. Audit Trails
Audit trails meticulously record every instance of data access, modification, or sharing. Each action is time-stamped and associated with the specific individual or system making the change. Here’s how this feature directly impacts patient engagement:
- Empowering Patients with Visibility: Assuring patients that their data activities are tracked and logged creates an open environment. Knowing “who accessed what and when” gives patients confidence in their information security.
- Addressing Concerns Promptly: Healthcare providers can quickly investigate and address patient concerns about data usage with a precise log of activities. This responsiveness builds a stronger relationship and promotes continuous engagement.
- Trustworthy Patient Data Management: Patients’ knowledge that their data is handled with a high level of accountability encourages them to share more accurate and detailed information.
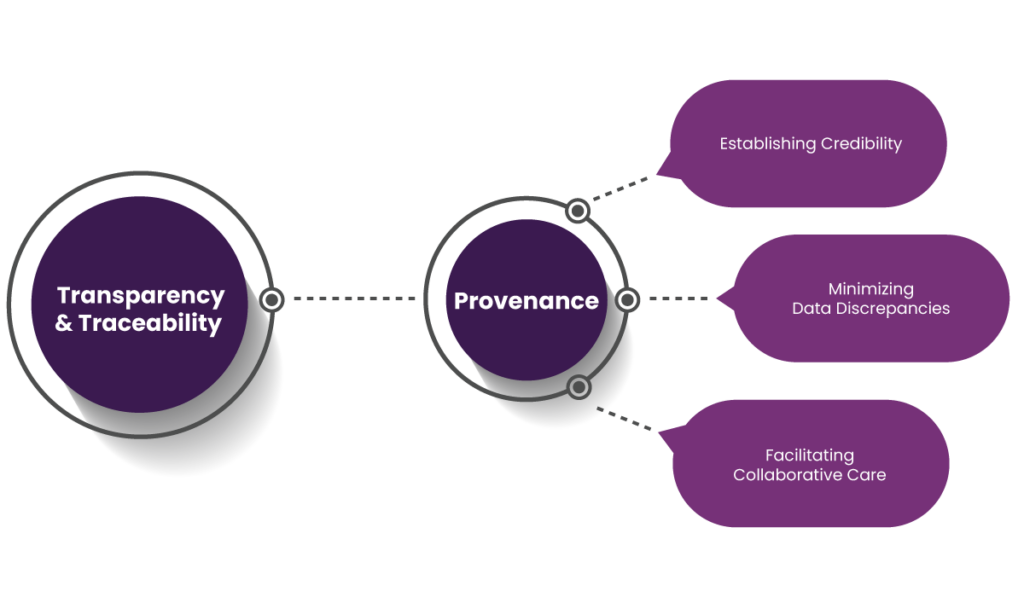
b. Provenance
Provenance refers to the ability to track the origin and flow of data. This feature enhances the authenticity of patient information by capturing how data moves through various systems and stakeholders. Here’s how it positively impacts patient engagement:
- Establishing Credibility: When patients know their data’s journey—from collection to usage—is verifiable, they feel more secure. This transparency drives them to participate actively in digital health initiatives like patient portals, telehealth, and remote monitoring systems.
- Minimizing Data Discrepancies: Provenance helps reduce errors by tracing inconsistencies back to their origin. As a result, patients are more likely to trust and use digital platforms for appointment bookings, lab results, and consultations.
- Facilitating Collaborative Care: Provenance tracks data flow across multiple providers, Provenancesupporting a collaborative approach to healthcare. Therefore, patients benefit from cohesive care plans and are motivated to stay involved in their treatment journey.
How PULSE Facilitates Interoperability While Maintaining Strict Compliance
PULSE prioritizes seamless data exchange while upholding the highest data security and privacy standards. Here’s how:
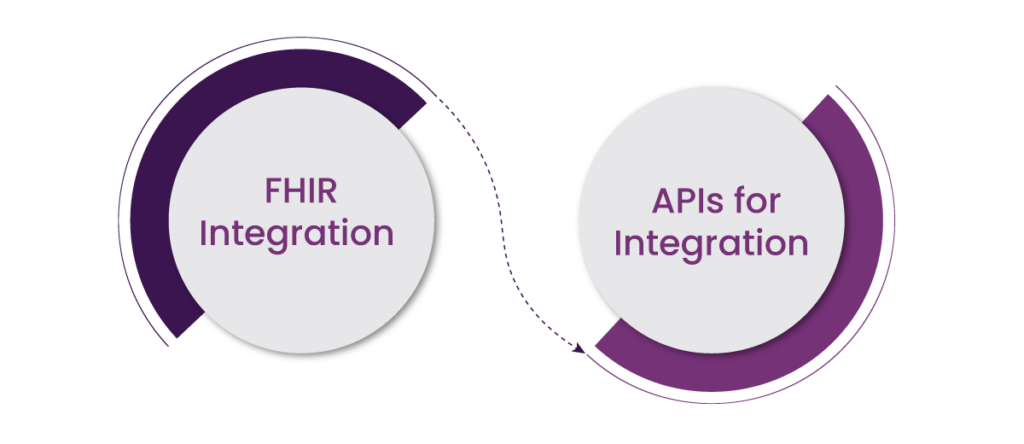
a. FHIR Integration
Fast Healthcare Interoperability Resources (FHIR) is a global standard for exchanging healthcare information electronically. By leveraging FHIR standards, PULSE enables patient data to flow seamlessly between platforms. This capability supports real-time access to critical information, such as medical history, lab results, and treatment plans.
This translates to a more cohesive experience for patients. Instead of re-explaining their medical history at every appointment or carrying physical records, they benefit from a unified health profile accessible to all their care providers.
b. APIs for Integration
PULSE features APIs which help connect diverse healthcare applications and IoT devices. Therefore, healthcare providers can integrate patient monitoring devices, electronic health records (EHRs), telehealth platforms, and wearable technologies into a single ecosystem.
For example, patients tracking heart rate or blood sugar with wearables can have their data instantly updated in their healthcare provider’s system. Therefore, physicians can monitor patient progress remotely and adjust treatments based on real-world data if required.
Workflow of the Patient-Provider Unified Ledger
Here’s how each step in the workflow contributes to boosting patient engagement:
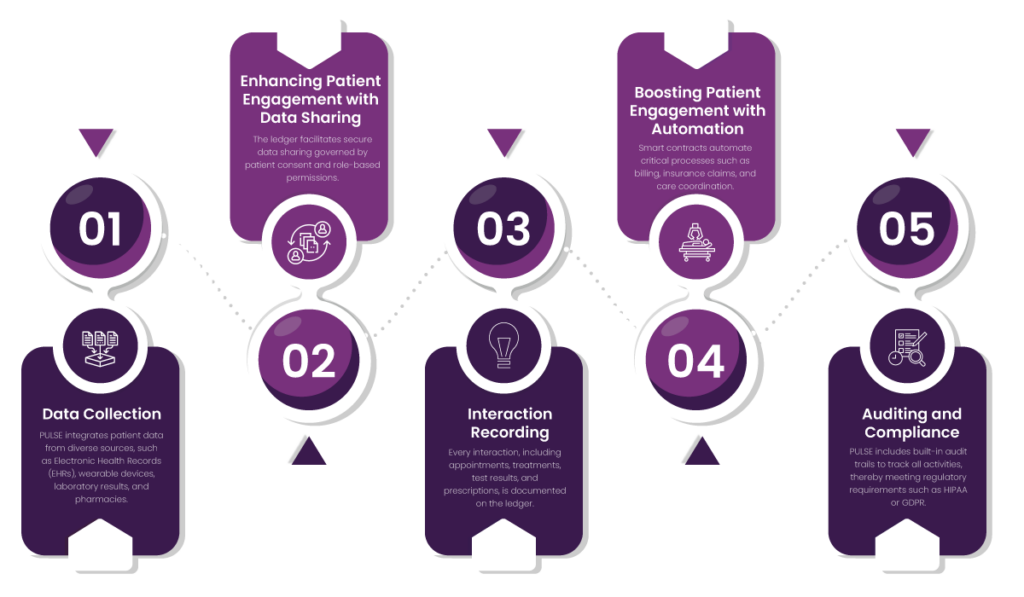
1. Data Collection
PULSE integrates patient data from diverse sources, such as Electronic Health Records (EHRs), wearable devices, laboratory results, and pharmacies. This comprehensive data collection gives providers a holistic view of a patient’s health journey. Additionally, the ability to include data from wearables and other personal health devices helps patients to track their overall health metrics.
2. Enhancing Patient Engagement with Data Sharing
The ledger facilitates secure data sharing governed by patient consent and role-based permissions. This process grants patients complete control over who accesses their information and for what purpose. Such a transparent system cultivates trust between patients and providers, thus encouraging patients to engage in conversations about their health without fear of data misuse.
3. Interaction Recording
Every interaction, including appointments, treatments, test results, and prescriptions, is documented on the ledger. This comprehensive log enables patients to review their medical history at any time, which helps them better understand their treatment plans and progress. Thus, by giving patients a clear and accessible record of their healthcare interactions, the system empowers them to ask informed questions, discuss alternative treatments, or provide care feedback, deepening their engagement and satisfaction.
4. Boosting Patient Engagement with Automation
Smart contracts automate critical processes such as billing, insurance claims, and care coordination. This automation reduces administrative burdens and frees up time for healthcare providers to focus on direct patient care. For patients, the elimination of delays in claims processing or appointment scheduling creates a smoother experience.
5. Auditing and Compliance
PULSE includes built-in audit trails to track all activities, thereby meeting regulatory requirements such as HIPAA or GDPR. While these compliance measures are critical for safeguarding data privacy, they also play a key role in building patient confidence. As a result, patients feel reassured knowing their data is being handled securely and ethically.
Final Thoughts
In an era where patient data is a cornerstone of modern healthcare, secure data management is not just a regulatory requirement but a foundation for building trust and improving care outcomes. By adopting advanced technologies like PULSE, healthcare providers can create a secure, interoperable ecosystem that prioritizes data privacy and empowers patients. From leveraging distributed ledger technology for tamper-proof records to integrating wearable devices and EHRs seamlessly, PULSE redefines how patient data is managed. Its innovative approach to Encryption, role-based access control, and audit trails ensures that providers and patients benefit from a transparent, efficient, and secure healthcare system.
The future of healthcare lies in digital transformation, and solutions like PULSE pave the way for safer, more connected care experiences. Contact us today and learn how PULSE can upgrade your patient data management practices and revolutionize your healthcare operations.
FAQs
1. Why is secure patient data management critical in healthcare?
Secure patient data management is essential to protect sensitive information such as medical histories, personal details, and insurance data from cyber threats. It safeguards patient privacy, builds trust, and prevents legal and financial repercussions for healthcare providers. Additionally, secure data management enhances communication and collaboration within healthcare ecosystems, which leads to better patient outcomes.
2. What are some key regulatory frameworks for patient data protection?
Key regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States and the General Data Protection Regulation (GDPR) in Europe, outline strict guidelines for handling, storing, and sharing patient information. These frameworks are designed to maintain patient privacy and provide healthcare organizations with a structured approach to data security and compliance.
3. How does Encryption protect patient data?
Encryption converts sensitive patient data into unreadable formats, making it accessible only with the correct decryption key. Technologies like Advanced Encryption Standard (AES) and Transport Layer Security (TLS) safeguard data during transmission and storage, protecting it from unauthorized access even if intercepted by malicious actors.
4. What role does role-based access control (RBAC) play in data security?
RBAC assigns permissions to users based on their specific roles within an organization. This limits access to sensitive information, allowing healthcare professionals to access only the data they need for their duties. For example, a billing officer may view financial records but not medical histories, thus reducing the risk of accidental or intentional data misuse.
5. What is the principle of least privilege, and how does it improve data security?
The principle of least privilege restricts user access to the minimum level necessary for performing their tasks. For instance, a medical intern might only review patient charts for educational purposes without editing treatment plans. This approach reduces vulnerabilities by limiting exposure to sensitive data and minimizing potential misuse.
6. How do audit trails contribute to secure patient data management?
Audit trails maintain a detailed record of every instance of data access, modification, or sharing. Each activity is time-stamped and linked to the individual or system responsible. These logs enable healthcare organizations to promptly identify and address potential security issues while reassuring patients about the secure handling of their data.
7. What is PULSE, and how does it enhance patient data management?
PULSE is a patient-provider unified ledger leveraging distributed ledger technology (DLT) to create a comprehensive record of patient-provider interactions. It offers features like immutable records, advanced Encryption, role-based access control, and audit trails, which collectively improve data security, interoperability, and patient engagement.
8. What is the significance of transparency and traceability in patient data management?
Transparency and traceability allow healthcare organizations to track data access and flow across various systems and stakeholders. Features like Provenance and audit trails give patients visibility into how their data is used, which improves data accuracy and care quality.
9. How do APIs and interoperability standards like FHIR support healthcare ecosystems?
APIs (Application Programming Interfaces) enable seamless integration between diverse healthcare applications, such as electronic health records (EHRs), telehealth platforms, and wearable devices. FHIR (Fast Healthcare Interoperability Resources) standards facilitate real-time data sharing, allowing healthcare providers to access a unified view of patient information. This integration enhances care coordination, reduces redundancies, and creates a more cohesive patient experience.
10. How does PULSE balance decentralization with centralized patient data management?
PULSE employs distributed ledger technology to maintain a unified data framework while eliminating monopolistic control over patient data. This approach enhances transparency and accessibility, allowing multiple stakeholders to collaborate securely while keeping patient records consistent and reliable.