The FHIR (Fast Healthcare Interoperability Resources) standard has revolutionized how healthcare data is shared and accessed. However, with great interoperability comes the great responsibility of securing that data.
Whether you’re a developer building healthcare apps, a hospital admin managing EHRs, or a policymaker designing compliance rules—understanding how to manage access to FHIR data is non-negotiable.
In this blog, we’ll break down the three core elements of FHIR data security—Users, Clients, and Permissions—and explain how platforms like Fusion can make this complex process easier, smarter, and more secure.
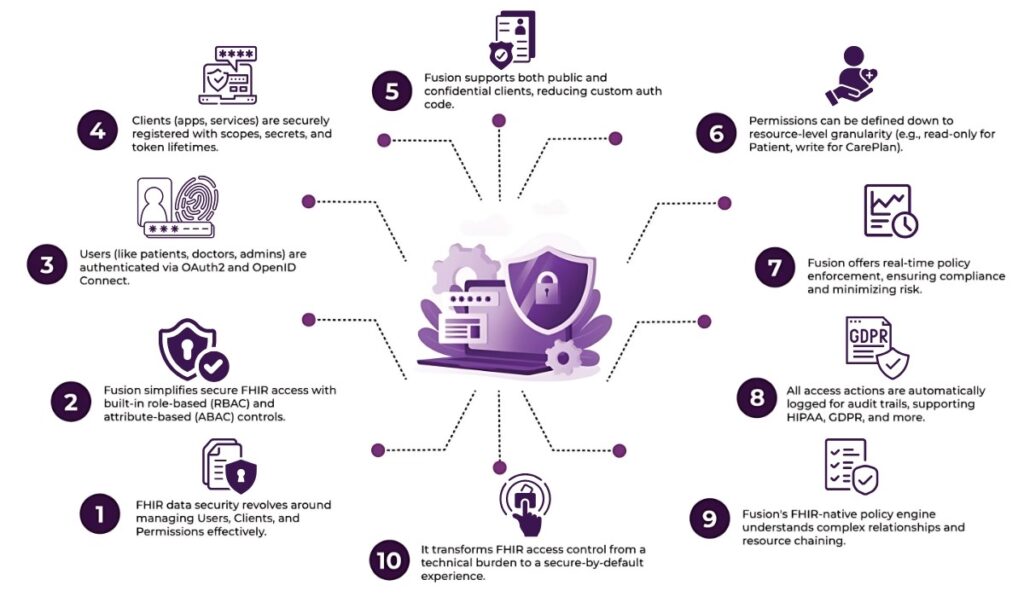
Table of Contents
Why FHIR Data Security Matters
Healthcare data is among the most sensitive information anyone can possess. And with the rise of digital health platforms, mobile apps, and EHR integrations, securing that data has never been more urgent.
Consider this: in 2022 alone, over 61% of healthcare data breaches were caused by unauthorized access. That’s not just a technical problem—it’s a violation of trust.
Let’s not forget compliance. From HIPAA in the U.S. to GDPR in Europe and India’s DPDP Act, modern regulations mandate strict access controls and transparency in how data is accessed, used, and shared.
Patients trust healthcare providers to keep their data secure. So if your system is powered by FHIR, securing access isn’t a feature—it’s a requirement.
This is where Fusion steps in—to help teams manage access without writing thousands of lines of brittle security code.
Who Are the “Users” in FHIR?
In the FHIR ecosystem, a “user” can be a:
- Patient accessing their health data via a mobile app
- Clinician reviewing or updating patient records in an EHR
- Administrator managing billing, appointments, or infrastructure
- Researcher retrieving de-identified datasets for analytics
Each user has different needs and permissions. Traditional access control systems often treat them with generic roles, which leads to either too much access or unnecessary restrictions.
Fusion takes a role-based and attribute-based access control (RBAC + ABAC) approach. You can define user roles like “nurse”, “doctor”, “admin”, or “external auditor” and layer in additional conditions like department, location, or resource ownership.
For example:
A nurse in the Pediatrics department can only view records of patients under 18 assigned to that department.
Fusion uses OAuth2 and OpenID Connect (OIDC) for secure user authentication, integrating smoothly with Identity Providers like Okta, Azure AD, or Fusion’s built-in IAM system.
What Are “Clients” in FHIR?
A “client” refers to the application that accesses FHIR data on behalf of users or itself. This includes:
- Mobile apps for patients
- EHR systems used by clinicians
- Backend services for analytics or billing
Clients can be of two types:
- Public Clients: Apps without a secure storage backend (e.g., mobile apps)
- Confidential Clients: Apps that can securely store credentials (e.g., server apps)
Fusion provides a secure client registration system where each client gets a unique ID, secrets, scopes, and token lifetimes. Clients authenticate using OAuth2 flows like:
- Authorization Code
- Client Credentials
- Device Code (for IoT)
Fusion issues access tokens that represent the client identity, scopes (like read:Observation), and user context.
With Fusion, you don’t have to worry about writing custom token handlers or manually validating every request. It enforces access in real time based on the registered client scopes and associated permissions.
The Role of Permissions in FHIR
Permissions are at the heart of FHIR data security. FHIR defines granular resource-level access such as:
- Read-only access to Patient, Observation, or Medication
- Create/update access to Encounter or Appointment
- Deletion rights (usually reserved for admin roles)
Fusion lets you define fine-grained access policies using:
- Scopes (e.g., user/Patient.read, system/Condition.write)
- Access Rules tied to user roles and attributes
- Resource-level filters (e.g., only allow access to a patient’s own data)
Example: A therapist should only be able to read Patient, Observation, and Encounter records for patients assigned to them, and write notes in the CarePlan resource.
Fusion makes it possible to enforce these policies dynamically using context-aware rules.
Why Fusion is the Most Secure Way to Use FHIR
When it comes to working with FHIR (Fast Healthcare Interoperability Resources), security isn’t something you can afford to treat as an afterthought. With sensitive patient data, stringent compliance standards, and ever-growing digital threats, healthcare apps need a FHIR solution that’s built from the ground up with security at its core—not added on later.
That’s exactly what Fusion delivers.
Fusion isn’t just another FHIR server. It’s a secure-by-design platform purpose-built for modern healthcare environments. From user authentication to real-time policy enforcement, Fusion wraps every part of the FHIR access journey in enterprise-grade protection.
Let’s dive into what makes Fusion the most secure way to use FHIR:
1. User Authentication & Authorization – Built-In and Rock-Solid
Fusion handles user identity and access management natively. That means no third-party plugins or fragile integrations to verify users. Whether it’s patients accessing their records, doctors writing notes, or billing admins managing claims, Fusion ensures every user is authenticated and authorized using robust OAuth2 flows.
You can define roles (like doctor, nurse, patient, admin), tie them to permissions, and rely on Fusion to enforce access—automatically and securely. It’s not just about who gets in; it’s about what they can do once inside.
2. Secure Client Registration with OAuth2 Support
In FHIR, clients represent applications—mobile apps, web portals, back-office systems—that interact with your healthcare data.
Fusion supports both public and confidential clients out of the box. This includes:
- Built-in support for OAuth2 token issuance and validation
- Secure credential storage and refresh token management
- Automatic scope handling based on client and user roles
No need to build custom token servers or maintain separate auth modules. Fusion provides everything your clients need to connect securely and stay compliant.
3. Fine-Grained Permissions—Down to the Resource Level
Most FHIR servers offer basic access control. Fusion takes it to the next level with fine-grained, real-time permission enforcement.
You can define access rules based on:
- User roles (e.g., a therapist vs. a patient)
- Resource types (e.g., Patient, Observation, Encounter)
- Actions (read, write, search, delete)
- Context (e.g., only allow access to a patient’s own records)
For example:
- A patient can read only their own Patient and Observation resources.
- A provider can update CarePlan for assigned patients but not delete Condition data.
This precision allows you to create nuanced, secure data access models without writing complicated backend logic. Fusion enforces policies in real-time, so there’s no lag or loophole.
4. Complete Audit Trails & Real-Time Access Monitoring
Compliance isn’t just about preventing unauthorized access—it’s also about proving that you did.
Fusion automatically logs every request, including:
- Who made it
- What resource they accessed
- What action they attempted
- Whether the action was allowed or denied
- When it happened
This audit trail is essential for regulatory standards like HIPAA, GDPR, and NDHM (India’s Health Data Management Policy). It also helps you track usage patterns, detect anomalies, and respond faster to incidents.
No more blind spots. With Fusion, you have a full, searchable log of every data touchpoint.
5. FHIR-Native Policy Engine—Not Just Another Wrapper
Many platforms treat FHIR like just another REST API. But Fusion understands FHIR deeply and natively.
Its access control engine is designed around FHIR’s unique structures and semantics—such as:
- Resource references and chaining (Patient -> Encounter -> Observation)
- FHIR scopes and compartments (to limit access based on patient context)
- FHIR terminology (to apply rules based on coded data)
This gives you context-aware access control that’s accurate, scalable, and ready for real-world healthcare complexity. Fusion is aware of FHIR relationships and applies permissions with full understanding of how resources are linked.
Fusion = FHIR + Enterprise-Grade Access Control
Let’s face it—bolting security onto a FHIR implementation after development is risky, expensive, and error-prone. Fusion eliminates that risk by embedding security and compliance into the DNA of your FHIR platform.
You don’t need to:
- Write custom middleware to manage access
- Maintain a separate audit logging service
- Worry about token expiration or credential leaks
- Re-implement access control logic for every new app
With Fusion, it’s all included—and it’s all secure.
Case study
Imagine you’re building a mental health support app that connects patients with therapists.
- Therapists need to access patient history and add notes.
- Patients should only see their own data.
- Admins should manage appointments and billing.
With Fusion:
- Define roles: therapist, patient, admin
- Register the mobile app as a public client
- Define fine-grained permissions for each role
Fusion enforces access in real-time, with OAuth2 tokens validating each request
No need to reinvent the wheel. No fragile access logic buried in your backend code. Fusion does the heavy lifting.
Final thoughts
Securing access to FHIR data isn’t just about ticking a compliance checkbox—it’s about protecting the heart of modern healthcare: patient trust. Whether you’re building an app, managing an EHR system, or setting data governance policies, the stakes are high. Missteps in access control can lead to data breaches, regulatory penalties, and, most importantly, a breakdown in the trust between patients and providers.
Fusion brings clarity, control, and confidence to FHIR security. With its robust user and client authentication, fine-grained permissions, native understanding of FHIR semantics, and built-in audit capabilities, Fusion enables healthcare organizations to secure sensitive data without the complexity.
In short, Fusion turns FHIR access control from a daunting challenge into a streamlined, secure-by-default experience. If you’re working with FHIR, don’t just connect your data—protect it. Let Fusion be the shield that keeps your healthcare ecosystem secure, scalable, and compliant from day one.
FAQs
1. What is FHIR and why is securing access to it important?
FHIR (Fast Healthcare Interoperability Resources) enables seamless data exchange in healthcare. Securing it protects sensitive patient data and ensures compliance.
2. Who are considered “users” in the FHIR ecosystem?
Users include patients, clinicians, administrators, and researchers—each requiring different access levels based on their roles and responsibilities.
3. What are “clients” in FHIR, and how do they differ from users?
Clients are applications (like mobile apps or EHR systems) that access FHIR data on behalf of users or independently, using secure authentication flows.
4. How does Fusion handle user authentication and authorization?
Fusion uses OAuth2 and OpenID Connect to manage user identity, define roles, and enforce secure, real-time access based on dynamic policies.
5. What types of permissions can be set in Fusion for FHIR data?
Permissions can include read, write, update, or delete rights at a granular level—defined by role, resource type, user attributes, or contextual conditions.
6. How does Fusion ensure secure client registration and token handling?
Fusion registers each client with unique credentials, enforces scope limitations, and handles token issuance, validation, and expiration securely.
7. Can Fusion help with regulatory compliance like HIPAA or GDPR?
Yes, Fusion provides detailed audit trails, fine-grained access control, and real-time monitoring to meet compliance standards across regions.
8. What makes Fusion different from other FHIR access control solutions?
Fusion is secure-by-design, FHIR-native, and eliminates the need for custom access logic. It integrates authentication, authorization, and auditing seamlessly.