In an environment where data moves constantly between people, businesses, and organizations, securing sensitive information has never been more critical. Without encryption, data transmission is highly vulnerable. But how does encryption keep our information safe during transmission? In this blog, we’ll discuss how encryption works in secure data exchange software and why it’s an absolute must today.
Table of Contents
What is Data Exchange Software?
Data exchange software refers to applications and platforms that facilitate the transfer of information between systems, applications, and users. These systems, designed to send, receive, and process data, enable seamless communication across various networks.
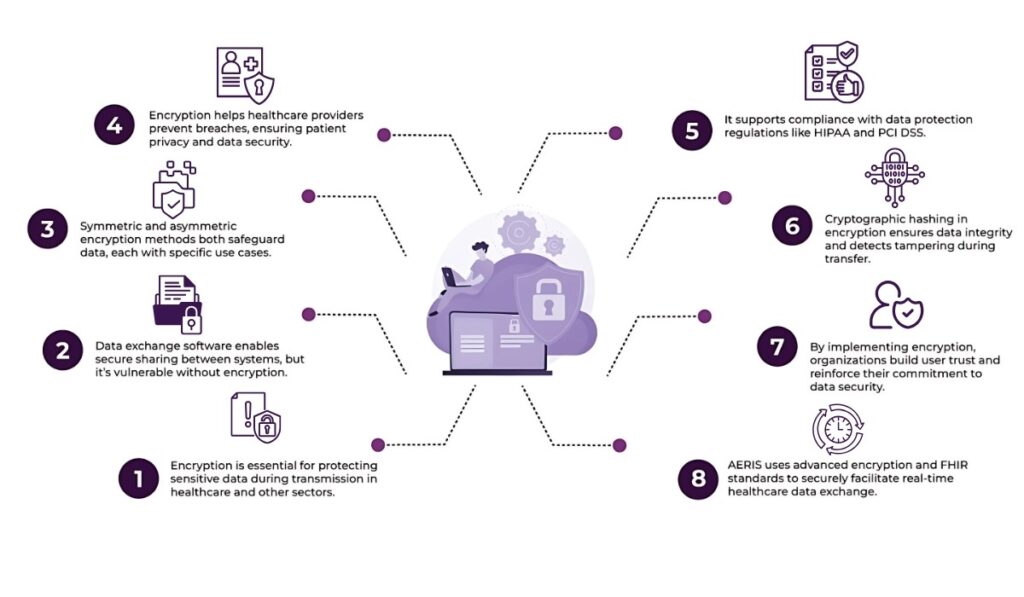
However, transferring vast amounts of data across different systems comes with the risk of exposure. Without the right security measures, data exchanged between entities can be intercepted, manipulated, or stolen. This is where encryption comes into play.
The Basics of Encryption
Encryption is a technique for converting readable data, known as plaintext, into an unreadable format, known as ciphertext. This process is achieved through complex algorithms that transform the data using a key, which is typically a string of characters. Only authorized parties with the correct decryption key can convert the ciphertext to its original form. Encryption aims to make data unreadable to unauthorized individuals, even if intercepted during transmission.
There are two main types of encryption:
- Symmetric Encryption: This type uses a single key for both encryption and decryption. The same key is shared between the sender and receiver, meaning both parties must keep the key secure. The main challenge with symmetric encryption is the safe distribution of the key.
- Asymmetric Encryption: This type uses two keys—a public key and a private key. The public key encrypts the data, while the private key decrypts it. The public key can be shared openly, while the private key remains confidential. This method enhances security by reducing the need to share sensitive information.
Both types of encryptions secure data, but their application varies depending on the context and the specific needs of the data exchange system.
Why Encryption is Vital in Data Exchange Software
1. Protection Against Data Breaches in Healthcare
Today, hackers constantly look for ways to access sensitive information such as patient records, medical histories, billing details, etc. A single data breach can seriously harm the individuals and healthcare organizations responsible for safeguarding it.
Encryption provides a robust defense against these attacks. Even if cybercriminals manage to intercept the data in transit, encryption renders it virtually useless without the decryption key. This makes it much harder for attackers to access or misuse the data, thus helping maintain patient privacy and trust.
2. Compliance with Regulatory Requirements
Data privacy laws and regulations, such as HIPAA, PCI DSS, etc., mandate that organizations take specific steps to safeguard sensitive data.
Encryption plays a key role in helping organizations meet these compliance requirements. By encrypting data before it is shared, healthcare organizations can ensure they are following proper data protection practices and fulfilling regulatory requirements. Without encryption, sensitive patient data could be exposed, which may lead to violations of important regulations and serious consequences.
3. Ensuring Data Integrity in Healthcare
The integrity of patient data is critical in healthcare. However, it can be vulnerable to tampering during transmission. For example, hackers might intercept the data, alter it, and send it as if it were legitimate, which could have serious consequences for patient care and safety.
To prevent this, encryption uses cryptographic hashing techniques to create unique codes tied to the original data. If the data is tampered with, the recipient can easily detect it because the hash code will no longer match. This process ensures that healthcare data remains accurate, secure, and trustworthy throughout transmission.
4. Building Trust with Users and Clients
Trust is one of the most valuable commodities in the digital world. Whether you are dealing with financial transactions, medical records, or intellectual property, clients and users need to trust that their data is secure when they exchange it with your systems.
By implementing encryption in your data exchange software, you send a clear message to your users: you are committed to protecting their information. This builds confidence and encourages users to engage with your platform, knowing their personal data is safeguarded. Moreover, organizations that prioritize data security are often seen as more reliable and responsible, which can ultimately lead to stronger customer relationships and business growth.
5. Preventing Man-in-the-Middle Attacks in Healthcare
A man-in-the-middle (MITM) attack happens when a hacker secretly intercepts communication between two parties, such as a patient and their healthcare provider. The attacker can alter, steal, or redirect sensitive information like medical records, insurance details, or personal health data, which can lead to serious privacy and security issues.
However, when healthcare communications are encrypted, a hacker can’t read or use the information because it’s scrambled. Likewise, digital signatures and certificates verify the identity of both parties, thus securing communication and preventing unauthorized access. These methods are vital for keeping patient information safe and secure.
How AERIS Protects Healthcare Data with Encryption
AERIS, a FHIR-based real-time data exchange software, uses advanced encryption technology to safeguard healthcare data and maintain the highest level of privacy.
AERIS employs cutting-edge encryption protocols to secure healthcare data as it moves between systems. By encrypting data at rest and during transmission, AERIS guarantees that the data remains unreadable and unusable even if an unauthorized entity intercepts the communication.
In addition to encryption, AERIS uses FHIR (Fast Healthcare Interoperability Resources) standards, which promote secure and efficient data exchange between healthcare systems. With FHIR-based encryption, AERIS helps healthcare organizations meet industry regulations like HIPAA while upholding the trust and confidentiality that patients expect.
Combining real-time data exchange capabilities with strong encryption methods, AERIS provides a seamless and secure way for healthcare providers to share patient data. This approach reduces the risk of data breaches and keeps sensitive health information safe throughout the exchange process.
Final Thoughts
Encryption is the backbone of secure data exchange in healthcare, whether it’s protecting against data breaches, meeting regulatory requirements, or building trust with patients.
With its real-time data exchange capabilities, AERIS takes this protection a step further. By using advanced encryption technologies alongside FHIR standards, AERIS ensures that healthcare organizations can securely share patient data without compromising confidentiality or integrity.
Contact us today to learn how AERIS can revolutionize your data exchange solutions!
FAQs
1. What is data exchange software?
Data exchange software allows the transfer of information between different systems, applications, and users, facilitating smooth communication across networks.
2. How does encryption protect healthcare data during transmission?
Encryption converts readable data into an unreadable format. Only authorized parties with the correct decryption key can access the original information, keeping it safe from hackers.
3. How does AERIS protect healthcare data?
AERIS uses advanced encryption protocols to secure healthcare data both during transmission and when stored. This prevents unauthorized access to sensitive health information.
4. Can AERIS be used by all healthcare organizations for secure data exchange?
Yes, AERIS is designed to facilitate secure data exchange for healthcare organizations of all sizes, providing real-time capabilities and robust encryption for protecting patient information.
5. What is FHIR and how does it help with secure data exchange?
FHIR (Fast Healthcare Interoperability Resources) is a standard that promotes secure, efficient, and interoperable data exchange between healthcare systems. It works alongside encryption to protect patient data.