In the fast-paced corporate world, innovation meets strict regulations; compliance is not just necessary but the very foundation of credibility. Imagine a busy office building from clients and contractors to interviewees and auditors. Every visitor is an opportunity and a responsibility. How does your organization handle the delicate balance of welcoming guests while safeguarding sensitive data and ensuring compliance?
Scribbled names in dusty logbooks are history. The data-driven era, marked by digital transformation, dictates effective visitor interaction management. And it’s not just being convenient; it’s about complying with standards set worldwide: GDPR, C-TPAT, ITAR, and FSMA, among others, which call for intense scrutiny of data privacy, security, and transparency.
A visitor management system is not just a tool but a connection between operational efficiency and regulatory adherence. It redefines how organizations monitor, record, and regulate visitor access, turning potential compliance challenges into opportunities for excellence. Be it ensuring data minimization, enforcing access control, or streamlining audits, and a robust VMS doesn’t just keep you compliant; it makes you stand out as a forward-thinking enterprise.
This blog explores visitor management as a critical piece for corporate compliance, discussing how the proper system will help businesses negotiate complexity in regulations, safeguard and improve data privacy, and provide a secure environment conducive to trust. In today’s corporate world, compliance is no longer just a checklist but a foundation for success- sustainable and profitable success.
So, let us unfold how visitor management translates compliance from a burden into an advantage for business.
Table of Contents
What are corporate compliances?
Corporate compliance is how a company follows all the laws and regulations that apply to its business. This generally involves designing, implementing, and monitoring policies, training, procedures and practices. Corporate compliance programs are grounded in creating formal policies to prevent violations of laws, training personnel on relevant regulations, implementing compliance procedures, and monitoring for violations. Your company is open to serious risk and legal liability without these elements.
Let’s take one hypothetical example-
ABC Corporation installed a Visitor Management System to streamline its visitor check-in process and ensure compliance with privacy laws. Before implementing the system, they faced challenges with paper-based logs, making it difficult to track visitors and comply with data protection regulations like GDPR.
With the VMS in place, all visitor data is securely captured and stored in the cloud, protecting personal information such as names, contact details, and visit history. The system automatically ensures that this data is only accessible to authorized personnel, reducing the risk of a data breach and meeting legal data security requirements.
Additionally, the VMS tracks the time of check-in and check-out, which is crucial for creating audit trails. Suppose a visitor’s access to sensitive areas is questioned. In that case, the company can quickly pull up the logs to verify the exact time they entered and left, providing a reliable record that can be used for legal purposes.
In case of an emergency, the system generates real-time reports on everyone currently on-site, which helps with evacuation planning and compliance with workplace safety laws. Moreover, the system’s electronic consent forms ensure visitors acknowledge the company’s policies, providing legal protection in case of any disputes.
Understanding Visitor Management Systems (VMS) on compliances.
Visitor management systems (VMS) must comply with a variety of legal and regulatory frameworks, each designed to address specific aspects of data privacy, workplace safety, and security. These regulations ensure an organisation’s smooth functioning and demonstrate accountability and trustworthiness to clients, employees, and stakeholders.
The Nature of Compliance
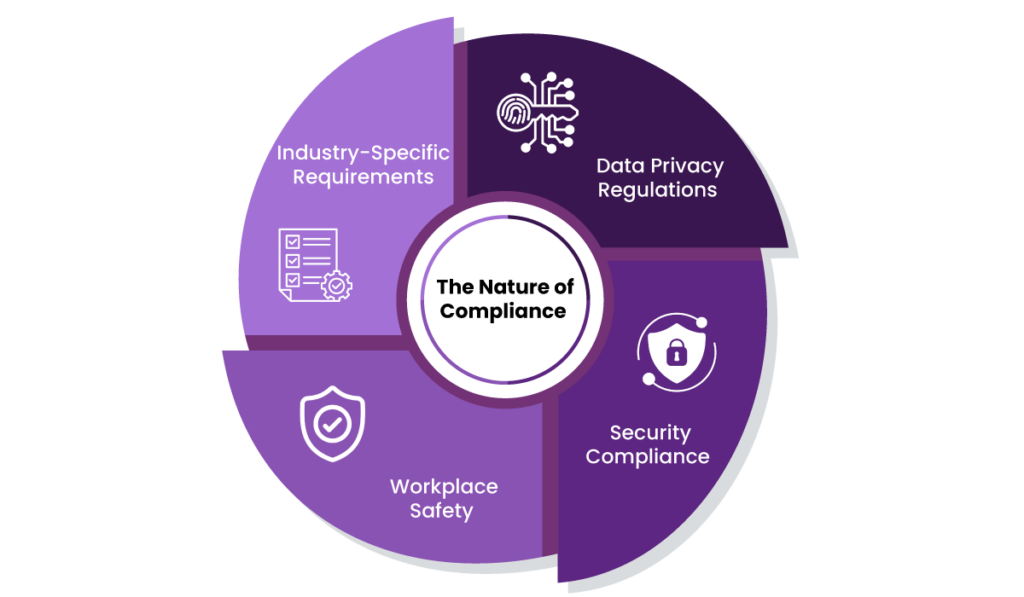
Visitor management compliance spans multiple domains:
- Data Privacy Regulations: Laws like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) aim to protect personal and sensitive information. For visitor management, this means ensuring that all visitor data is collected, processed, and stored in ways that respect individual privacy rights. Organizations must also provide transparency about how this data will be used and ensure its security.
- Security Compliance: International Traffic in Arms Regulations (ITAR) and Customs-Trade Partnership Against Terrorism (C-TPAT) focus on preventing unauthorized access to sensitive areas, especially in industries like defence and logistics. A VMS helps enforce these requirements by verifying visitor identities and restricting access to specific zones.
- Workplace Safety: The Occupational Safety and Health Administration (OSHA) mandates safe and secure work environment protocols. A visitor management system aids compliance by tracking who is on-site, ensuring they are briefed on safety rules, and facilitating emergency evacuations.
- Industry-Specific Requirements: Standards like the Food Safety Modernization Act (FSMA) in the food industry and System and Organization Controls (SOC 2) for data integrity in technology services add layers of specific compliance measures. Visitor management systems ensure that every visitor complies with these operational requirements, from hygiene standards in food facilities to secure data handling in IT environments.
Why Visitor Management Needs to Incorporate Compliance
Compliance in visitor management is critical for several reasons:
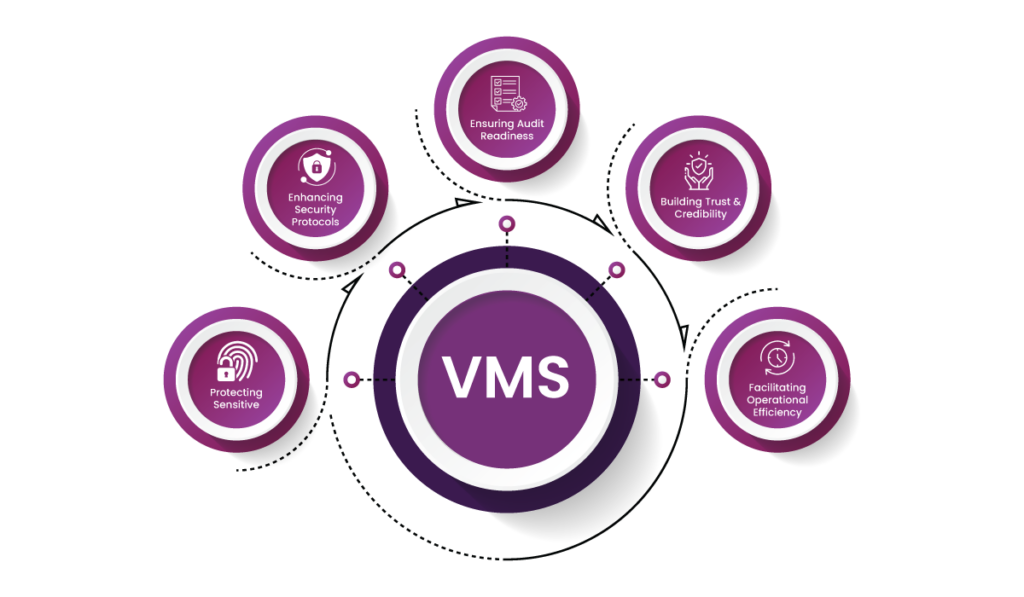
- Protecting Sensitive Data: Modern organizations often deal with highly sensitive data, whether it pertains to intellectual property, personal health information, or trade secrets. A VMS ensures this data is protected from unauthorized access, aligning with regulations like GDPR and HIPAA. Non-compliance could lead to hefty fines, lawsuits, and reputational damage.
- Enhancing Security Protocols: Compliance with standards like ITAR and C-TPAT relies on controlling who enters and exits sensitive facilities. A visitor management system ensures robust identity verification and access logging, reducing the risk of breaches or unauthorized access that could lead to legal repercussions.
- Ensuring Audit Readiness: Regulations such as SOC 2 require detailed documentation of all access points and visitor interactions. A VMS generates real-time logs and comprehensive reports, simplifying the audit process and ensuring organizations can demonstrate compliance effortlessly.
- Building Trust and Credibility: Compliance is not just about avoiding penalties—it also reassures stakeholders that the organization prioritizes security, safety, and ethical practices. A compliant visitor management system reflects an organization’s commitment to upholding these values.
- Facilitating Operational Efficiency: By automating compliance processes such as data collection, consent management, and safety briefings, a VMS reduces administrative burdens. This allows organizations to focus on their core operations while meeting regulatory requirements seamlessly.
Legal and Regulatory Requirements in Visitor Management
Visitor Management – VISTA Visitor management systems (VMS) must adhere to a range of legal and regulatory requirements, ensuring that organizations maintain operational security and efficiency and comply with strict laws governing data privacy, workplace safety, and industry-specific practices. Below is a detailed breakdown of key compliance acts and how they are integral to visitor management systems.
General Data Protection Regulation (GDPR)
The GDPR is a European Union regulation that protects personal data and ensures privacy. Enacted in 2018, it governs how organizations collect, store, and process personal data. Under GDPR, companies must obtain explicit consent from visitors before collecting personal information and ensure transparency about data usage. Non-compliance can result in fines of up to €20 million or 4% of annual global turnover.
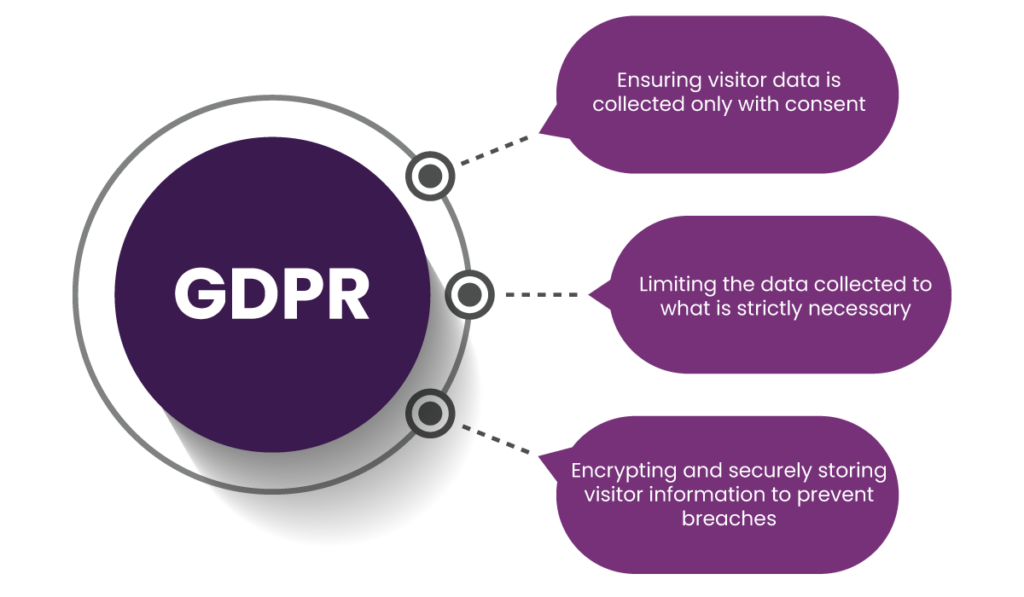
In visitor management, GDPR compliance involves:
- Ensuring visitor data is collected only with consent.
- Limiting the data collected to what is strictly necessary.
- Encrypting and securely storing visitor information to prevent breaches.
- Allowing visitors to access or request deletion of their data when required.
GDPR is critical for safeguarding individual privacy and fostering trust in organizations handling sensitive data.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is a U.S. law enacted in 1996 to protect sensitive health information and ensure its confidentiality. It applies to healthcare providers, insurers, and their business associates. A violation of HIPAA can result in fines ranging from $100 to $50,000 per violation, depending on the severity.
In the context of VMS, HIPAA compliance is essential for:
- Protecting patient confidentiality when visitors access healthcare facilities.
- Limiting access to areas with sensitive health data to authorized personnel only.
- Implementing robust security protocols to prevent unauthorized access to electronic health records (EHRs).
By securing visitor access to healthcare facilities, VMS ensures HIPAA standards are met and patient data remains protected.
Food Safety Modernization Act (FSMA)
The FSMA, introduced in the U.S. in 2011, emphasizes preventive measures in food safety to protect the public from contamination. It mandates stringent controls over food production and supply chains, including managing access to food facilities.
For VMS, FSMA compliance involves:
- Monitoring and restricting visitor access to areas where food is handled.
- Recording visitor information to trace potential contamination sources during audits.
- Ensuring all visitors comply with hygiene and safety protocols before entry.
FSMA ensures that visitor access does not compromise food safety, reducing risks to public health.
International Traffic in Arms Regulations (ITAR)
ITAR governs the export and handling of defence-related articles and services in the U.S., ensuring they do not fall into unauthorized hands. Organizations dealing with sensitive military technologies must comply to avoid severe penalties, including fines and revocation of licenses.
In visitor management, ITAR compliance includes:
- Verifying the identities of all visitors before granting access.
- Restricting entry to sensitive areas to authorized personnel only.
- Maintaining detailed logs of visitor activities for accountability.
Compliance with ITAR prevents unauthorized access to sensitive defence information, safeguarding national security.
Occupational Safety and Health Administration (OSHA)
OSHA, established in the U.S. in 1970, promotes workplace safety by enforcing standards to prevent injuries and illnesses. Non-compliance can result in fines of up to $15,625 per violation.
For VMS, OSHA compliance involves:
- Tracking on-site visitors during emergencies to ensure safe evacuations.
- Providing safety briefings to visitors before entering hazardous areas.
- Keeping records of visitors to identify potential exposures during incidents.
A compliant VMS ensures a safer workplace, aligning with OSHA’s goals of reducing workplace risks.
Customs-Trade Partnership Against Terrorism (C-TPAT)
C-TPAT is a voluntary U.S. program aimed at strengthening supply chain security. Participants must monitor visitor activities and interactions at their facilities to ensure supply chain integrity.
VMS supports C-TPAT compliance by:
- Managing and documenting visitor access to secure areas.
- Enhancing visibility into visitor interactions at entry and exit points.
- Providing audit-ready records to demonstrate adherence to security protocols.
By ensuring supply chain security, VMS aids organizations in protecting global trade networks.
System and Organization Controls 2 (SOC 2)
SOC 2 is a framework for ensuring data security and integrity in cloud-based service providers. It requires strict access controls and monitoring to protect sensitive data.
In visitor management, SOC 2 compliance involves:
- Implementing access controls to prevent unauthorized data exposure.
- Generating detailed logs of visitor activities for audit purposes.
- Ensuring data handling processes align with SOC 2’s five trust principles: security, availability, processing integrity, confidentiality, and privacy.
SOC 2 compliance establishes an organization’s credibility in maintaining data security.
Benefits of Visitor Management in Compliance
A robust Visitor Management System (VMS) maintains corporate compliance by bridging the gap between operational efficiency and regulatory adherence. Its implementation ensures businesses meet stringent legal requirements while creating a secure, transparent, and streamlined process for handling visitors. Here’s how a VMS transforms compliance into a strategic advantage:
1. Reinforced Data Security
Data privacy is a critical concern for any organization. With regulations like GDPR in place, securing visitor information is non-negotiable. A VMS encrypts sensitive data and stores it securely, ensuring restricted access to authorized personnel only. This minimizes the risk of breaches while fostering trust with clients and stakeholders.
2. Automated Audit Trails
Audits are a significant aspect of corporate compliance. A VMS simplifies the process by maintaining detailed, time-stamped records of all visitor activity. These logs provide transparency and make demonstrating compliance during inspections or regulatory reviews easier, saving time and effort.
3. Stringent Access Control
By integrating with access control systems, a VMS ensures that visitors are granted entry only to areas they are authorized to access. This level of control enhances security and aligns with industry standards like ITAR or HIPAA that demand restricted access to sensitive environments.
4. Transparency and Accountability
Real-time notifications and visitor tracking provide organizations with complete visibility into visitor movements. This transparency is invaluable for complying with frameworks like C-TPAT, which emphasize supply chain security and operational accountability.
5. Operational Optimization
Beyond compliance, a VMS streamlines visitor check-in processes, reducing wait times and enhancing the overall visitor experience. Automated workflows ensure consistent adherence to protocols, reducing the likelihood of human error and improving efficiency.
Incorporating a VMS strengthens compliance and establishes an organization as a proactive and trustworthy entity in the eyes of clients, partners, and regulators.
How VISTA Improves Visitor Management to Enhance Workplace Compliance
In a world where regulatory frameworks shape the operations of modern organizations, compliance is no longer optional; it’s integral to building trust and sustaining business success. Visitor management is a critical aspect of this compliance puzzle. VISTA’s Visitor Management System (VMS) ensures that organizations meet and exceed the stringent requirements of workplace regulations.
From safeguarding data privacy to streamlining access controls, VISTA offers a comprehensive solution that simplifies visitor handling and strengthens your organization’s compliance posture. Here’s how VISTA makes a difference:
1. Centralized Data Management for Improved Privacy
Data privacy laws like GDPR, CCPA, and HIPAA mandate that organizations protect personal information from unauthorized access and misuse. VISTA’s VMS ensures compliance by securely collecting, encrypting, and storing visitor data. The system limits data access to authorized personnel, preventing breaches and ensuring adherence to global privacy standards. Furthermore, VISTA supports data minimization practices by capturing only the information necessary for compliance purposes and automating data purges by retention policies.
2. Streamlined Visitor Screening
Compliance frameworks such as ITAR and FSMA require rigorous control over who can access a workplace. VISTA’s advanced visitor screening capabilities enforce security by cross-referencing visitor details against watchlists or pre-set criteria. Whether it’s a supplier, auditor, or contractor, VISTA ensures only pre-approved and legitimate visitors gain entry, thereby maintaining workplace safety and compliance.
3. Robust Audit Trails and Reporting
Auditing is at the heart of regulatory compliance, but it can be time-consuming and error-prone when managed manually. VISTA eliminates these challenges with automated audit trails that capture detailed records of every visitor interaction, including check-in times, identification details, and areas accessed. These logs are easily accessible and can be exported to meet the requirements of compliance inspections or internal reviews, ensuring a seamless auditing process.
4. Enhanced Access Control
Workplace compliance often involves managing access to sensitive areas, particularly in healthcare, manufacturing, and IT sectors. VISTA integrates seamlessly with access control systems to ensure visitors can only enter authorized areas. For example, a meeting visitor cannot access restricted production facilities or server rooms. By reducing the risk of unauthorized access, VISTA aligns with industry-specific regulations like HIPAA, ITAR, and C-TPAT.
5. Real-Time Notifications and Transparency
Transparency is a cornerstone of compliance. VISTA’s real-time visitor tracking and notification features inform employees about visitor movements, enhancing situational awareness and accountability. This level of visibility ensures that organizations can maintain compliance with frameworks like C-TPAT, which emphasize secure and transparent operations.
6. Simplified Onboarding and Training
Educating staff on proper visitor management is crucial for organisations navigating complex compliance landscapes. VISTA provides intuitive interfaces and customizable workflows that reduce the learning curve and ensure employees adhere to compliance protocols. Pre-defined templates and automated processes guarantee consistency, minimizing the risk of human error.
7. Alignment with Industry-Specific Requirements
Different industries face unique compliance challenges. VISTA tailors its features to meet sector-specific requirements, from protecting patient data in healthcare settings to ensuring supply chain transparency in manufacturing. By customizing workflows and reports to align with these regulations, VISTA provides a flexible and scalable solution for compliance.
Case Studies and Real-World Examples
The Challenge
With over 5,000 employees spread across multiple offices, the IT services company faced growing challenges in managing visitor flows while ensuring compliance with strict data privacy regulations like GDPR. HR and facility management teams were burdened by:
- Inefficient Processes: Manual visitor logs caused delays at reception, creating a poor first impression for candidates, clients, and vendors.
- Data Privacy Risks: Visitor information stored in physical logbooks posed a compliance risk and lacked proper security protocols.
- Access Control Issues: Managing and tracking visitor movements across sensitive areas was cumbersome, increasing security vulnerabilities.
- Audit Complications: Manually tracking and presenting visitor records during compliance audits consumed significant time and resources.
The Solution: Implementing VISTA
The HR and facility management teams implemented VISTA’s Visitor Management System (VMS) to address these challenges and modernize their visitor handling processes.
Key Features Adopted:
- Digital Check-In: Touchless registration for visitors with real-time notifications for hosts.
- Data Encryption: Secure storage of visitor data to meet GDPR compliance.
- Integrated Access Control: Permission-based access to specific areas of the facility.
- Automated Audit Trails: Detailed visitor logs for compliance and reporting.
The Impact
- Streamlined Visitor Experience: HR reported a 40% reduction in check-in times, creating a seamless onboarding process for job candidates and external guests. VISTA’s intuitive interface allowed visitors to pre-register, saving time and leaving a positive impression of the company.
- Enhanced Compliance and Data Security: Facility managers noted an immediate improvement in data privacy practices. VISTA ensured that all visitor information was encrypted and accessible only to authorized personnel, reducing the risk of data breaches and maintaining full GDPR compliance.
- Improved Security and Access Control: With VISTA’s integration with the company’s access control systems, HR could regulate who entered meeting rooms, server areas, and other restricted zones. Unauthorized access incidents dropped by 25%, boosting overall workplace safety.
- Simplified Audit Processes: During a recent GDPR audit, the facility management team successfully presented detailed visitor records with just a few clicks. What previously took hours was accomplished in minutes, saving time and reducing stress during compliance inspections.
- Operational Efficiency: The facility team reduced administrative overhead by 30% by eliminating manual logbooks. Staff could now focus on strategic tasks instead of managing visitor documentation.
Conclusion
Visitor management is about more than just tracking who walks through your doors. It’s about creating a secure, compliant, efficient environment that inspires trust. A robust system like VISTA can turn compliance from a burden into a competitive advantage, paving the way for sustainable and profitable success.
Compliance isn’t just a checklist; it’s the foundation of modern business. Make VISTA your partner in bridging the gap between innovation and regulation, ensuring every visitor interaction aligns with your commitment to excellence.
FAQs
What is Corporate Compliance?
Corporate compliance ensures that a company follows all applicable laws, regulations, and industry standards, safeguarding it from legal risks and liabilities.
How does Visitor Management relate to Corporate Compliance?
Visitor management plays a crucial role in compliance by regulating visitor access, protecting sensitive data, ensuring safety, and adhering to various regulatory frameworks.
What regulations must a Visitor Management System (VMS) comply with?
A VMS must comply with data privacy laws like GDPR, security regulations such as ITAR and C-TPAT, workplace safety laws like OSHA, and industry-specific regulations like FSMA and HIPAA.
How does a VMS help with GDPR compliance?
A VMS helps comply with GDPR by collecting visitor data with explicit consent, limiting data collection, ensuring secure storage, and providing transparency about data usage.
Why is Data Privacy important in Visitor Management?
Data privacy ensures that visitors’ sensitive personal information is protected, minimizing risks of breaches and complying with regulations like GDPR and HIPAA.
What are the key benefits of using a VMS for compliance?
A VMS enhances data security, streamlines audit trails, enforces access control, ensures transparency, and optimizes operational efficiency while keeping the organization compliant with regulations.
How does VMS ensure workplace safety compliance?
A VMS ensures that visitors are briefed on safety protocols, tracks who is on-site during emergencies, and helps with evacuation procedures, supporting OSHA compliance.
What is the role of VMS in security compliance?
A VMS verifies visitor identities, restricts access to sensitive areas, and maintains access logs, ensuring compliance with security standards like ITAR and C-TPAT.
How does VISTA enhance Visitor Management compliance?
VISTA improves compliance by centralizing data management, streamlining visitor screening, and providing automated audit trails, ensuring data privacy and security regulations adherence.
How does VISTA ensure data privacy?
VISTA encrypts visitor data, limits access to authorized personnel, and supports data minimization practices, ensuring compliance with global privacy regulations like GDPR and HIPAA.
What is the importance of audit trails in compliance?
Audit trails help organizations maintain transparent, time-stamped records of all visitor interactions, simplifying compliance during audits and regulatory reviews.
How does VISTA improve visitor screening?
VISTA cross-references visitor details against watchlists and pre-set criteria, ensuring only authorized individuals can access sensitive areas, thus enhancing security and compliance.
What specific compliance regulations does VISTA support?
VISTA supports GDPR, HIPAA, ITAR, C-TPAT, OSHA, FSMA, and other industry-specific regulations by ensuring secure visitor data handling and access control.
What are the consequences of non-compliance in Visitor Management?
Non-compliance can lead to hefty fines, legal liabilities, reputational damage, and security breaches, making a compliant visitor management system essential.
How does a VMS contribute to operational efficiency?
A VMS reduces administrative burdens by automating processes like visitor check-in, data collection, and consent management, allowing organizations to focus on core operations while ensuring compliance.