A digital revolution is sweeping through healthcare, with patient data now flowing seamlessly across systems. This incredible shift is mainly due to FHIR (Fast Healthcare Interoperability Resources). But with this newfound connectivity comes a critical question: how do we protect sensitive health information without slowing down care? Because the balance between easy access and robust security is no longer just an option—it’s important for saving lives.
If you’re working with FHIR data or collaborating with a FHIR software development company, understanding how to secure access at every level — including users, clients, and permissions — is required. In this blog, we discuss the best practices and technologies for safeguarding FHIR data.
Understanding FHIR and Its Security Landscape
FHIR is a modern healthcare data standard developed by HL7 to enable seamless and secure data exchange between health systems, applications, and devices. It incorporates built-in security features such as support for OAuth 2.0, SMART on FHIR, and encrypted communication protocols to help protect sensitive health information.
However, while FHIR provides a strong framework for secure interoperability, the actual security of any FHIR-based system depends on how these features are implemented. Without proper security architectures and controls, sensitive personal health information (PHI) may still be at risk of unauthorized access, which can lead to privacy breaches, legal consequences, and loss of patient trust.
Therefore, a FHIR software development company must not only focus on building functional applications but also prioritize designing and enforcing robust security measures to safeguard healthcare data.
Table of Contents
Key Areas to Focus on When Securing FHIR Data
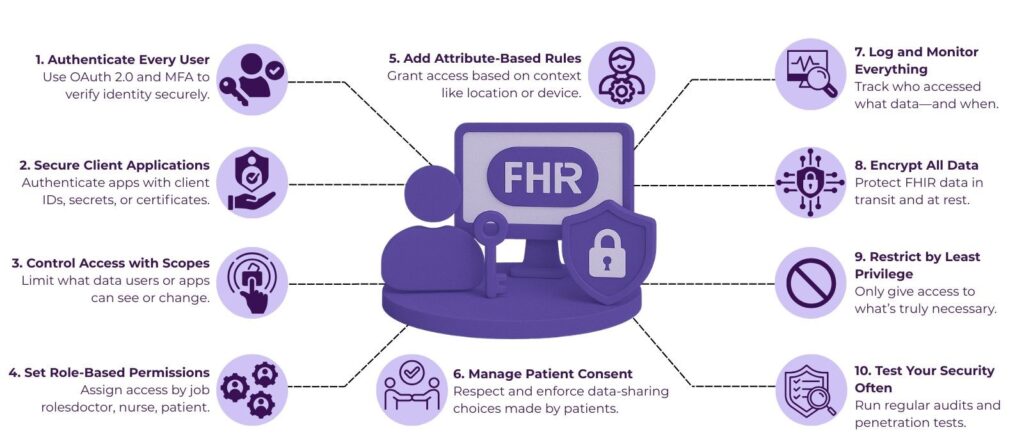
Securing FHIR data involves multiple layers:
- Authentication of users — confirming identities of individuals accessing the system.
- Client authentication — verifying the applications or devices making requests.
- Authorization and permissions — defining what data each user or client can access and what actions they can perform.
- Audit and monitoring — tracking access and changes to data for accountability.
- Data encryption and transport security — protecting data in transit and at rest.
1. User Authentication
User authentication confirms the identity of a person attempting to access FHIR resources. Some common authentication methods include:
- Username and password: The most basic form, but often insufficient alone due to risks of phishing and weak passwords.
- Multi-factor authentication (MFA): Combines something the user knows (a password) with something they have (a phone app or hardware token) or something they are (biometrics).
- OAuth 2.0 and OpenID Connect: Widely adopted in healthcare apps for token-based authentication that avoids repeatedly sending credentials.
- Smartcards and certificates: Often used in enterprise healthcare environments to provide hardware-backed identity.
Role of OAuth 2.0 in FHIR Security
OAuth 2.0 is a crucial protocol for securing FHIR APIs. It allows users to authenticate through a trusted identity provider and grants applications a scoped access token rather than exposing user credentials. This token grants temporary access to FHIR data, and scopes limit what can be accessed.
Many FHIR software development companies implement OAuth 2.0 alongside OpenID Connect for a modern, flexible authentication system that supports Single Sign-On (SSO) and MFA.
2. Client Authentication
In a FHIR ecosystem, it’s not just the users but also the clients — apps, devices, or services — that access the data. These clients must be authenticated to prevent unauthorized software from harvesting patient information.
a. Types of Clients
- Confidential clients: Apps that can securely store credentials (like server-based applications).
- Public clients: Apps that cannot securely store secrets (such as mobile or single-page apps).
b. Securing Clients with OAuth 2.0
Clients request access tokens from the authorization server using credentials or authorization codes. Confidential clients use client IDs and secrets, while public clients often rely on dynamic client registration or Proof Key for Code Exchange (PKCE) to prevent interception attacks.
A FHIR software development company typically implements strict client registration processes, including validating redirect URIs and defining allowed scopes, to reduce risks.
c. API Keys and Certificates
For certain scenarios, API keys or client certificates may be used for client authentication. While API keys are simpler, certificates provide stronger security but require infrastructure for certificate issuance and management.
3. Permissions and Authorization
Authentication confirms identities, but authorization controls what those identities can do. This is where permissions come in — defining which FHIR resources a user or client can access, modify, or delete.
a. Scopes and Consent
OAuth 2.0 scopes specify access levels (read, write, etc.) and resource types. For example, a token with scope patient/Observation.read allows reading observations for a patient but not modifying them.
Patient consent can further restrict access, especially in jurisdictions with strict privacy laws. Therefore, implementing consent management within FHIR APIs adds an extra layer of control.
b. Role-Based Access Control (RBAC)
RBAC assigns permissions based on user roles such as doctor, nurse, admin, or patient. Each role has a predefined set of permissions, which simplifies administration and management.
For example, doctors may have full read-write access to a patient’s records, nurses may have read access to certain data, and patients can view only their personal data.
c. Attribute-Based Access Control (ABAC)
ABAC grants access based on attributes like location, device type, time of access, or emergency status. This allows more granular, dynamic access control.
For example, access might be granted to emergency responders only during an active emergency or to clinicians only when on the hospital network.
Best Practices for Securing FHIR Data Access
Here are some of the best practices that a trusted FHIR software development company follows to secure data access.
1. Use Strong, Modern Authentication
Avoid outdated or weak authentication methods. Employ OAuth 2.0 with OpenID Connect and implement MFA wherever possible.
2. Validate and Register Clients Rigorously
Control which applications connect to your FHIR server through strict client registration, verifying their identity and restricting scopes.
3. Limit Scopes and Permissions to Minimum Necessary
Apply the principle of least privilege by granting users and clients only the access they absolutely need to perform their functions.
4. Enforce Role and Attribute-Based Access Controls
Combine RBAC and ABAC to build flexible, context-aware authorization models that adapt to clinical needs and compliance requirements.
5. Implement Patient Consent Management
Respect patient choices by integrating consent policies into authorization decisions. Make consent records auditable and easily updateable.
6. Monitor and Audit Access Logs
Maintain detailed logs of who accessed what data and when. Regularly review logs to detect suspicious activity and comply with legal mandates.
7. Encrypt Data In Transit and At Rest
Use Transport Layer Security (TLS) to protect data moving over networks and encryption technologies to safeguard stored data.
8. Perform Regular Security Assessments
Conduct vulnerability scans and penetration testing to uncover weaknesses in authentication, authorization, and overall security.
Final Thoughts
Securing access to FHIR data is an ongoing journey involving careful design of authentication, client validation, and authorization processes. Therefore, choosing the right FHIR software development company is a strategic step to build a secure, compliant, and user-friendly FHIR implementation.
With modern protocols like OAuth 2.0 and SMART on FHIR, combined with strong role and attribute-based controls, securing FHIR data can become a streamlined, manageable part of your healthcare technology strategy.
If you want to discuss securing your FHIR data or building compliant healthcare apps, contact Helixbeat today.
FAQs
1. Why should I partner with a FHIR software development company like Helixbeat?
Partnering with a FHIR software development company like Helixbeat provides expertise in secure FHIR data management. Helixbeat offers customized solutions to enhance data security, streamline interoperability, and ensure compliance with healthcare regulations.
2. How does FUSION simplify auditability and compliance with FHIR systems?
FUSION maintains detailed access logs, capturing who accessed what data, when, and from which client. This audit trail streamlines compliance with privacy regulations, such as HIPAA, offering transparency and accountability for healthcare organizations.
3. How does FUSION handle permissions and authorization for users in healthcare applications?
FUSION supports role-based access control (RBAC) to define granular permissions for users. Therefore, clinicians and administrative staff only have access to the data they are authorized to view or modify.