Today, FHIR (Fast Healthcare Interoperability Resources) has emerged as the de facto standard for exchanging healthcare information electronically. It offers a modular, resource-based format that supports RESTful APIs, making data sharing between systems more agile and scalable.
But with great interoperability comes great responsibility.
As FHIR opens the gates to seamless data exchange, healthcare organizations must be equally committed to securing access to sensitive patient data. Unauthorized access or poor permission management can lead to HIPAA violations, data breaches, and loss of trust.
Let’s discuss how to secure FHIR data with a focus on users, clients, and permissions.
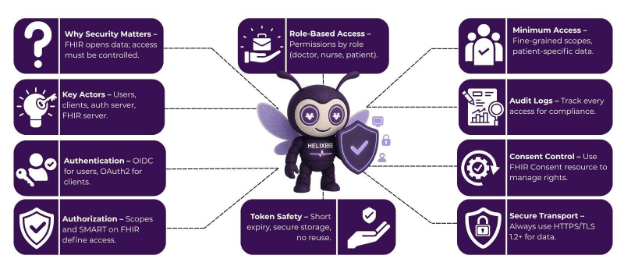
Table of Contents
1. Why FHIR Security Is a Top Priority
FHIR is built to make data portable. Systems using FHIR APIs can share medications, lab results, conditions, and more with just a few calls. But unlike legacy systems that kept data locked behind walls, FHIR makes data accessible, potentially to anyone who can hit the endpoint.
This openness is powerful, but you need to define who can access what, under what conditions, and with which identity.
2. Who Are the Actors?
Before jumping into implementation, you need to understand the main actors in the FHIR security ecosystem:
A. Users
Humans—clinicians, patients, administrators—who interact with the system through applications. Role-based permissions usually govern their access.
B. Clients
These are applications, services, or systems that act on behalf of users or autonomously. Clients can be mobile apps, EHRs, third-party analytics tools, or even public health systems.
C. Authorization Server
This is the service responsible for validating identities, issuing tokens, and enforcing access controls. It often follows the OAuth 2.0 standards.
D. FHIR Server
The system that stores and provides access to the actual FHIR resources. It responds to API requests, but only after authentication and authorization checks.
3. Step One: Authenticate First
Before any permission checks happen, the system needs to know who (or what) is making the request.
A. Human Users: OpenID Connect
FHIR servers commonly integrate with OpenID Connect (OIDC) for human user authentication. OIDC builds on OAuth 2.0 to provide identity information, like user profile data and roles.
Users typically log in via a secure login page, and upon success, receive an ID token and access token.
B. Clients: OAuth 2.0 Client Credentials Flow
For non-human clients, the client credentials flow of OAuth 2.0 is standard. The client authenticates itself using its client ID and secret, then obtains an access token.
These tokens are like digital passports that say, “I am who I claim to be—let me in.”
4. Step Two: Authorize the Right Way
Authentication confirms identity. Authorization decides what that identity is allowed to do.
FHIR security revolves around two key concepts:
A. Scopes
Scopes define what parts of the system a token can access. For example:
- patient/Observation.read: Read observations for the authenticated patient
- user/Condition.write: Write conditions for the logged-in user
- system/*.read: Read all data for a backend system
The access token includes a list of approved scopes, and the FHIR server uses this list to accept or deny requests.
Think of scopes as permission labels stamped onto tokens.
B. Smart on FHIR
This is a specification that extends OAuth 2.0 for healthcare use cases. SMART (Substitutable Medical Apps and Reusable Technologies) defines a consistent way to request authorization and scopes.
Apps that follow the SMART on FHIR framework plug into EHRs with minimal friction using standardized tokens, scopes, and flows.
5. Role-Based Access
Let’s say you have three users:
- Dr. Emily, a cardiologist
- Nurse Jake, a general nurse
- Sarah, a patient
Should they all have the same access? Definitely not.
This is where Role-Based Access Control (RBAC) comes into play. Each role has specific permissions:
FHIR servers often integrate with Identity and Access Management (IAM) platforms that assign roles to users and enforce permissions accordingly.
6. Keep Tokens in Check
Tokens are powerful. If they fall into the wrong hands, they can be used to access sensitive data.
Here’s how to keep them tight and secure:
- Set expiration times. Short-lived tokens reduce the window of misuse.
- Use refresh tokens wisely. Refresh tokens allow new access tokens without re-login, but should be securely stored.
- Avoid token reuse. Never allow the same token to be used across multiple sessions or clients.
FHIR servers should reject expired or tampered tokens immediately.
7. Limit Access to the Minimum Necessary
One of the core principles of data privacy is minimization—only give access to the data that’s required for a specific task.
In FHIR terms:
- Use fine-grained scopes. Don’t give system/*.* access if the app only needs patient/AllergyIntolerance.read.
- Filter responses by patient context. For example, a clinician treating Patient A shouldn’t see data from Patient B.
- Use compartment-based access. FHIR supports patient compartments, where data is grouped based on patient identity. You can limit clients to a specific compartment when possible.
8. Audit Everything
Security isn’t just about preventing breaches—it’s also about detecting them.
FHIR servers should log:
- Who accessed which resource
- What operation was performed (read, write, delete)
- When and from where the request was made
- Whether the request succeeded or failed
These logs are critical for forensic analysis, compliance reporting, and operational monitoring.
9. Don’t Forget About Consent
Patient consent is a legal and ethical cornerstone in healthcare. Before accessing or sharing data, applications may need to validate whether the patient has agreed.
FHIR provides a Consent resource that captures:
- Who gave consent
- What data is covered
- Who can access it
- Time limits and conditions
Consent can be embedded in access flows or managed separately by consent management platforms integrated with the FHIR server.
10. Secure the Transport Layer
All the access controls in the world mean nothing if the data is intercepted during transmission.
Use HTTPS—always.
Transport Layer Security (TLS) encrypts the data traveling between clients and servers. It protects tokens, patient data, and login credentials from being captured by man-in-the-middle attacks.
TLS 1.2 or higher is a must in any production-grade FHIR ecosystem.
FUSION: The FHIR Server Built for Seamless Healthcare Data Exchange
Whether you’re building a patient app, a provider portal, or a public health analytics platform, FUSION gives you everything you need to connect, access, and exchange health data—fast and reliably.
1. Fully Aligned with HL7 FHIR Standards
FUSION speaks fluent FHIR. Built from the ground up to support all major FHIR versions, it simplifies integration with EHRs, labs, pharmacies, and external systems—no matter their complexity.
2. Strong Access Control & Smart Authorization
With support for OAuth2, SMART on FHIR, and fine-grained scopes, FUSION helps you define exactly who gets access to what. Whether it’s a clinician, patient, or third-party app, permissions are tightly governed at every step.
3. Audit-Ready Logging & Compliance
FUSION tracks every interaction down to the resource level. Comprehensive audit trails give you visibility and peace of mind while meeting regulatory requirements like HIPAA and beyond.
4. Seamless Data Sharing
Break down silos. FUSION converts structured data into usable FHIR resources and allows smooth bi-directional exchange with HL7 v2, CDA, and other legacy formats through easy integration workflows.
Final Thoughts
FHIR has unlocked a new era of healthcare interoperability, but securing access to FHIR data is a layered process. It starts with identifying users and clients, and moving through authentication, scopes, roles, consent, and auditing. The strength lies in combining these layers into a resilient security posture that protects sensitive data without blocking innovation.
From startups to enterprise hospitals, FUSION is the FHIR backbone that keeps data flowing—securely, intelligently, and without friction. Want a demo? Get in touch with Helixbeat today!
FAQs
1. What role does OAuth 2.0 play in FHIR security?
OAuth 2.0 is the standard protocol used to authorize clients and users. It issues access tokens that carry permission details (called scopes) and are required for accessing FHIR APIs.
2. What is SMART on FHIR, and how does it help?
SMART on FHIR is a framework that extends OAuth 2.0 to healthcare-specific use cases. It simplifies the process of integrating third-party apps with EHRs while supporting standardized permission models.
3. How does role-based access control (RBAC) apply to FHIR?
RBAC assigns different permissions to users based on their role. For example, a doctor might be able to write diagnoses, while a patient can only view their own medical history.
4. Why is audit logging important in FHIR implementations?
Audit logs record who accessed what data, when, and from where. They help in detecting unusual activity, maintaining compliance, and performing forensic reviews if needed.